The Essential Eight – strategies to improve your cyber security
Security is an everyday task. I don’t mean its routine or low importance, but that it is crucial and needs attention everyday to keep your business, your people and your systems safe.
Security should not be about shutting the stable door after the horse has bolted. It should be proactive so that cyber-attacks don’t work in the first place. That’s why the Australian Cyber Security Centre (ACSC) has published The Essential Eight. Its not a standard or a framework, its a list of practical actions you can take so your systems and your people and your data are safer.
This article explains why The Essential Eight strategies matter and how they should be applied in your business.
Why another set of guidelines?
There are already so many security guidelines, frameworks, standards, why add another one? Whether you are a large business with demanding security requirements, or a business with very sensitive data, or a small business just starting out, The Essential Eight will help you meet your security requirements. With a clear path to progressive improvement through a maturity model, The Essential Eight can guide you to align at the level you need for your unique business circumstances. A key difference between The Essential Eight and other security guidance is that the strategies are all proactive and practical.
Cyber-crime is a real cost to Australian business
Here are some basic facts:
- If you don’t take positive action on cyber security, you will be targeted and you will be impacted.
- The ACSC estimates the cost of cyber-crime to Australian business at more than $30 billion per year https://www.cyber.gov.au/acsc/view-all-content/reports-and-statistics/acsc-annual-cyber-threat-report-july-2020-june-2021
- If your business “pivoted” during COVID to a more mobile workforce with flexible arrangements for working from home, you are of course in good company, everyone else did it too. The pandemic ushered in the largest, fastest business transformation ever seen – with inadequate planning that was often at the expense of security standards. It helped increase the opportunities for cyber-attack.
- Cyber crime has increased so much in the last few years, that even notoriously slow to react institutions are catching up: Government policy, ASIC, APRA, court judgements, insurers. The end result is that the focus has now shifted to holding business accountable for the security of their own systems and their Clients’ data.
Enter The Essential Eight
Its easy to follow the Essential Eight: it’s a practical list of how to configure your systems so they are a lot tougher on cyber crooks by proactively guarding against many of the most common attacks. There are eight areas to configure:
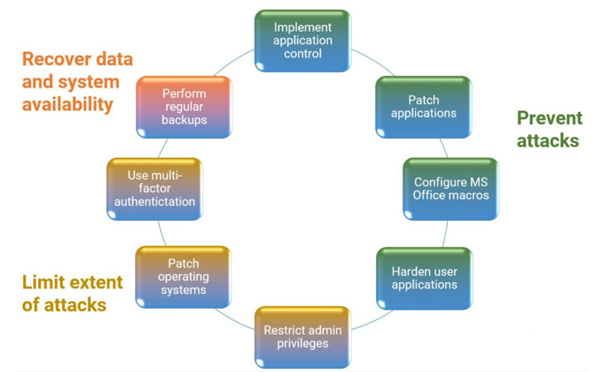
- The first four are about PREVENTING attacks.
- The second four are about LIMITING what an attack can do
If you implement all of these – and really do them, not just write them in a policy – then your systems will be much safer from attack. Simple as that.
How to implement The Essential Eight
The Essential Eight is designed for businesses to be able to follow a plan for implementing the strategies. The ACSC has provided a Maturity Model with three levels, using it any business can:
- See where they are at currently across all eight strategies
- Assess where their business needs to be to meet their particular requirements (based on their own risks and the sensitivity of the data they hold)
- Identify what the gaps are – and therefor have on hand a practical to do list that will bring the business into alignment with the Maturity Level the business wants to meet.
Here is an example:
One of the Essential Eight is “Patch Applications”. In summary, this strategy includes:
- Update applications with the latest security patches
- Remove any applications that are no longer supported
- Check devices regularly to confirm they are up to date
Here is what that looks like across the different maturity levels (I have included Level 0):
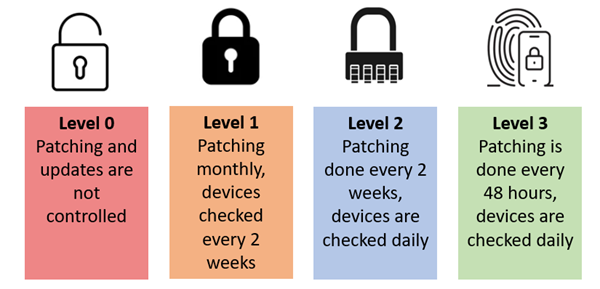
Each of the strategies has easy to understand guidance for each maturity level. In this example, you can see if you are a company with sensitive data or high needs for uptime, you most likely need to align with Level 3.
Not a do-it-yourself project
All the strategies require technical skills to implement and all of them require proper automation, monitoring and control to roll out and manage across your environment. They highlight the need for a good IT partner to support your business.
To implement the Essential Eight:
- Get a maturity level report
- Assess your risk and requirements (your business, your clients)
- Identify the gaps – by listing what you need to do to align with your identified Maturity Level
- Implement the list in easy steps
What will you get for your trouble?
Of the top 15 most successful types of cyber attack, The Essential Eight covers 10. Here is a list of those top 15:
- Malware (viruses on your computer)
- SQL injection (exploit attacking a database server)
- Zero-day exploit (brand new virus that nobody has heard of or seen before, so anti-virus programs don’t know about it)
- DNS Tunnelling (a way of attacking a computer to run malware on it)
- Business Email Compromise (stealing access to your mailbox)
- Cryptojacking (a hacker installs malware that allow them to secretly use your computer)
- Drive-by Attack (infected websites that malicious code through your browser to your computer)
- Cross-site scripting (XSS) attacks (malicious code on a website that can infect your computer when you use that website)
- Password Attack (guessing or otherwise stealing your password)
- AI-Powered Attacks (using artificial intelligence to massively speed up the ability to attack a lot of computers at once)
- Phishing (persuading people to take unsafe actions
- Man-in-the-middle attack (a fake site interposed between you and the site you think you are accessing)
- Distributed Denial-of-Service (DDoS) attack (a barrage of connections to a website done to overwhelm the site and make it inaccessible)
- Eavesdropping attacks (a hacker sniffs network traffic to pick up private data)
- IoT-Based Attacks (attack on unsecured non-computer devices such as printers to gain access to a network)
The first ten on the list can all be made safe by implementing The Essential Eight. The last five relate to websites, networks and people. You can fix these by:
- Doing regular cyber awareness training for your staff
- Protect your website and network
- Secure ANYTHING that can connect to the Internet
Your business needs to implement The Essential Eight – do it now!
FooForce can help you to do a Maturity Level assessment and assist with implementing The Essential Eight for your business. Contact us for a chat

