
Our experienced and skilled team of qualified security professionals deliver the full range of security consulting services to help you understand security priorities and manage your IT risk.
Security and consulting
| IT Strategy Alignment Align your IT to your business needs and goals |
| Cyber Risk Awareness Training is the number one most effective strategy to defend your business from cyber threats |
| Information Security Audit Regular, scheduled review is essential to confirm the controls you put in place are being applied and are effective. |
| Information Security Consulting Our expert consultants are at your service to provide advice, solutions and achievable strategies |
| Project Management We will plan, manage and implement your IT projects so that your business is not disrupted and the project delivers what you need |
| BCP/DR Services Disasters can happen anytime and to any business. Our job is to see that these don’t cause disruption, downtime, exposure and production loss. |
| Cloud security review The cloud is an extension of the office, and as vulnerable to mistakes, cost overruns, security failures. You need us on your side managing these risks to keep your business safe and productive. |
Some of our security related services
Identity Theft Monitoring
We go into the Dark Web to keep you out of it
We will constantly scan and monitor the Dark Web for compromised email credentials across your whole company and alert you so you can take action before your business has been exposed.
We will notify you immediately:
• if you have compromised email credentials on the Dark Web
• if your personally identifiable information (PII) is exposed and published eg date of birth, home address
• if the source of the breach is known eg social media
You can take immediate action to safeguard your information.
Book a scan of the Dark Web for your business today.
 Cyber Security Awareness Program
Cyber Security Awareness Program
The program starts with an engaging and interactive presentation which explores the global cyber threat and how this affects both individuals and organisations. It provides practical insights so your staff can protect themselves from common attacks and the cyber threat landscape is explained through real life case studies to highlight and reinforce the reality of these threats.
The initial onsite (or webinar) session presents relevant information about new or emerging cyber risk vectors and is within the reach of non-technical business users. It is particularly focused on bringing to top of mind the critical role of all staff as the first line of protection from cyber threats.
Both the initial presentation and follow-up sessions can be tailored to meet any specific needs of the business, and can be modified in scope and detail.
…
Program Outline:
Onsite presentation:
- Presenter is a highly experienced speaker with extensive knowledge of cyber risk
- Presentation and content is customised for the specific organisation and a copy of the presentation can be provided
- Duration 40 – 60 minutes (can be customised to meet time constraints)
Follow up:
- A dummy cyber attack (phishing simulation) can be run before and after the presentation to gauge staff engagement and learning
- Monthly cyber update to maintain awareness
- Follow up webinar six months after the session with updated material
The session and follow up is designed to provide attendees with:
- A greater level of awareness of the global cyber security threats and consequences for individuals and organisations
- A deeper understanding of the areas of greatest threat to themselves and their organisation
- Insights into the actions which should be taken to minimize cyber risks to themselves and the organisation
- Improved empowerment to participate as a cyber-defender as part of the organisation’s risk mitigation strategies
Representative topics which will be covered in the presentations include:
- Overview of Cyber Threats and Threat Actors
- Cyber-attack real life stories
- Email Security, Password Protection, Phishing and Downloads
- Malware, phishing and social engineering: how can we protect ourselves
- What to do if we suspect a suspicious activity
- Other topics to be agreed and specific to the organisation
Key Objective: Attendees will walk away with a sound and practical understanding of modern day cyber threats, how these represent themselves as an organisational threat, and their role in mitigating these threats as part of a cyber-risk mitigation strategy.
For more information or to arrange an initial discussion, please contact us
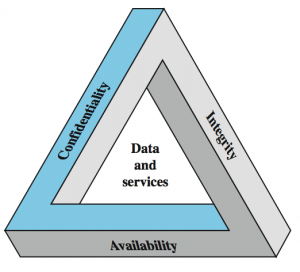 IT Audit and Risk Review
IT Audit and Risk Review
The FooForce team includes qualified auditors and risk professionals certified by ISACA and with more than five years’ experience working across security, risk and audit. FooForce is highly qualified to assist enterprises to develop appropriate IT standards. Our experience includes conduct of IT Reviews and Security and Compliance Audit services against industry accepted standards including COBIT5.
For your business to grow, you need to be able to manage risk: no risk, no profit, wrong risk, also no profit – and maybe no business! Risk and opportunity are hand in hand, but IT is risk not correctly managed can adversely impact your business goals. To manage IT risk you need a clear view of:
- Your IT assets and what they do
- What the risks are
- How IT contributes to business goals
…
IT risks are usually about one of these:
- Disclosure
- Misuse
- Disruption
We will scope and conduct an IT review focusing on your specific needs and giving you the information you need to make decisions around how to manage your IT related risks.
Our team will work with you to protect business value and enhance the effectiveness, quality and value from your IT systems. With a deep understanding of IT business risk, we can help reduce risk, improve performance and bring greater value to your company.
IT Audit is specialised, requiring extensive skills and experience, worldwide industry accreditation, exacting education and qualification standards. Most IT companies don’t have accredited IT Auditors, these are usually only found in the large enterprise organisations. FooForce does have accredited auditors so we can give you enterprise value but without the enterprise sized price tag.
FooForce IT and Security Review Will Help You:
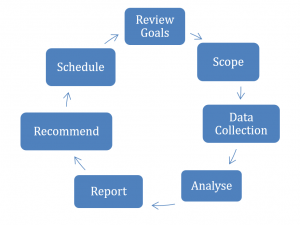 Make informed business decisions:
Make informed business decisions:
- IT Systems must be available when needed so that business decisions are timely and accurate.
- The IT systems must be protected against all types of losses and disasters so that business continuity can be assured.
- The IT audit reviews how well IT is aligned with business goals and recommends improvements.
- Business development is enhanced when the resources available are clearly known.
Better safeguard IT assets:
- Information is a critical asset of a company and its protection and management should be a priority.
- Information should be disclosed only to those who have a need to see and use it and not to anyone else.
- Assurances must be available that no unauthorized modification can be made to the data or the software in the systems.
Gain improvements in governance:
- Quality audits assist with corporate governance by reviewing relevant compliance requirements for the company for information storage, privacy, use of personal data etc.
- Regulatory responsibilities can be met for a range of stakeholders including shareholders, suppliers, customers, communities and governments as well as related contractual agreements and policies.
Save money through productivity and efficiency gains:
- Efficiency and productivity is enhanced when business processes are properly supported by IT. The audit identifies areas where changes are needed to make more efficient use of IT to support business processes and priorities.
- Operational excellence can be achieved through reliable, efficient application of technology.
Optimize the IT budget:
- The IT Audit reviews services and technology against accepted industry standards so the company can identify possible areas where costs can be reduced.
- Planned IT projects should be reviewed to ensure these properly align with business goals.
 Internal and External Security And Penetration Testing
Internal and External Security And Penetration Testing
With cyber attacks becoming the norm, it is important to undertake regular vulnerability scans and penetration testing. The FooForce suite of services and tools will enable you to identify vulnerabilities and ensure on a regular basis that the cyber controls are working. The full scope of the penetration testing will:
- Determine weaknesses in the infrastructure (hardware), application (software) and controls.
- Test controls have been implemented and are effective – this provides assurance as to information security and demonstrates compliance and cyber resilience to your Board and senior management.
- Test applications that may be avenues of attack.
- Discover known and new vulnerabilities in existing systems, processes and user awareness.
Critically, the activities and tools employed by FooForce in these services are not intrusive for staff and will not affect productivity during the testing period.
The combination of testing and exposing potential vulnerabilities across infrastructure, web and cloud assets, wireless networks and, importantly, staff awareness and behaviour helps you to:
- Identify the resilience of your infrastructure security controls and the ways an attacker might gain unauthorised access and control and provides you with visibility on the security vulnerabilities within your infrastructure that could be exploited in an attack.
- Assess the key components of your web applications and supporting infrastructure, including how these components are deployed and how they communicate with users and server environments to highlight the security of applications that broker access to critical data.
- Detect access points and rogue devices, analyse your configurations, and test for vulnerabilities so that you can implement security controls to prevent an attack.
- Identify whether your employees are vulnerable to phishing emails, enabling you to take immediate remedial action to improve your cyber security posture and particularly make clear where you need to apply internal security awareness and how your organisation reacts to attempts to compromise your staff.

